To answer the question of why we seek justice and revenge, we first need to understand the evolution of the tendency in humans to form cooperative coalitions. This is because it’s this phenomenon only that gives rise to contexts in which we seek justice and revenge.So why do we form cooperative coalitions at all?Why do people come together and work together?The fundamental condition to be met for the formation of a cooperative coalition is that there must be some common goals that the coalition is trying to achieve. The attainment of these goals must benefit each member of the coalition in some way. If a member of a coalition feels that the goals of his coalition are not in line with his own goals then obviously he will decide to break free from the coalition.In short, it’s the gains that motivate people to form coalitions and stay in them.Ancient coalitionsIn our ancestral times, forming cooperative coalitions helped our ancestors to hunt large animals, share food, invade territories, build shelters and defend themselves better. Those who formed coalitions had an evolutionary advantage over those who didn’t.Hence, those possessing the psychological mechanism of coalition formation out-reproduced those who didn’t. The result being that more and more members of the population were willing to form cooperative coalitions.Today the people who desire to form coalitions far outnumber those do not possess any such desire to the point ‘forming alliances’ is considered by many as the fundamental attribute of human nature. The point is that the psychological mechanism of forming coalitions has made its way into our psyche because it had myriad benefits.But the full story about coalition formation in humans isn’t so simple and rosy…Justice, punishment, and revengeWhat if some members of a coalition are defectors and free riders i.e. they take away only the benefits without contributing anything or even incurring huge losses to other members of the group?Such members will have a huge fitness advantage over those who’re loyal to the coalition. Also, when huge costs are incurred over other members they’d doubtless want to break free from the coalition, and the coalition will get torn apart.So the presence of defectors and free riders will work against the evolution of the psychological tendency to form cooperative alliances. If such a tendency has to evolve, there must some opposing force that keeps defectors and free riders in check.This opposing force is the human psychological desire for justice, punishment, and revenge. The desire to punish those who’re disloyal toward the coalition helps keep disloyalty in check which in turn facilitates the evolution of the tendency to form cooperative coalitions.We frequently witness the human desire for justice, punishment and revenge not only throughout history but also in our day to day lives. When strict punishments are in place for those who fail to contribute their fair share, high levels of cooperation tend to emerge. Add to this the desire to harm slackers and those who’ve incurred a heavy cost on others. This, in common language, is called revenge. Studies have shown that people’s reward centres of the brain are activated when they punish or observe punishment of those who they think deserve punishment. Revenge is indeed sweet.
The desire to punish those who’re disloyal toward the coalition helps keep disloyalty in check which in turn facilitates the evolution of the tendency to form cooperative coalitions.We frequently witness the human desire for justice, punishment and revenge not only throughout history but also in our day to day lives. When strict punishments are in place for those who fail to contribute their fair share, high levels of cooperation tend to emerge. Add to this the desire to harm slackers and those who’ve incurred a heavy cost on others. This, in common language, is called revenge. Studies have shown that people’s reward centres of the brain are activated when they punish or observe punishment of those who they think deserve punishment. Revenge is indeed sweet.
Blind Athletes Provide Clues About the Nature of our Emotions
 By Melanie Tannenbaum for Scientific American
By Melanie Tannenbaum for Scientific American
One of the most important ways that we learn how to interact with the world around us is through observational learning. By watching how our friends and family members behave, we learn at a very young age how to do things like turn on a lightbulb, open a door, or play with a doll, without having to suffer through a tedious trial-by-error reinforcement process every single time we need to learn how to do something new. It’s only natural to assume that we have similarly learned when to smile politely, how to wrinkle our noses in disgust, or why we should furrow our brows in anger by watching the people around us react in those ways when presented with similar emotionally-evocative situations.
But what if observational learning isn’t the only way in which we figure out how to express our emotions? What if those emotional expressions — or at least, some of them — actually come “pre-programmed” into our very nature, and we would make those grimaces, brow-furrows, and polite smiles of thinly-veiled contempt without ever once seeing others make those expressions first?
In a recent study, David Matsumoto and Bob Willingham studied photographs from the Judo competition in the 2004 Olympic Games to examine the athletes’ facial expressions. Predictably, the researchers found that gold and bronze medalists were more likely to display broad smiles and patterns of facial muscle activation that signal genuine happiness, whereas silver medalists were more likely to display “fake” smiles or expressions of contempt and disgust.
This effect had been found in research before, and it wouldn’t have been particularly noteworthy, had it not been for one important fact:
Approximately half of the athletes in the photos were blind. In fact, half of the blind athletes had been so since birth, meaning they had never directly observed another person’s emotional expressions.
Not only did both congenitally and noncongenitally blind athletes spontaneously produce emotional facial expressions after winning or losing, their expressions were practically identical to those of the sighted athletes. The blind athletes — even those who had never been able to see for a single day in their lives — not only displayed genuine smiles after winning, they also displayed expressions of contempt or politely fake smiles after losing. Somehow, without ever having seen another person’s face, they still knew what to do with their own faces when they won or lost. For researchers who had been arguing that emotions are “hardwired” and emotional displays like smiles or frowns are biologically determined (rather than learned through culture or social interactions), this finding was a big-time win.
The researchers acknowledge that the congenitally blind athletes’ expressions still could have been socially conditioned. Family members and friends could have verbally reinforced appropriate expressions throughout their lives, so this study is not necessarily proof that emotional displays are completely biologically hardwired. However, this study does show that observation is not necessary in order to learn emotional display and regulation. And, for whatever it’s worth, close others would not be able to verbally reinforce appropriate emotional displays if the blind individuals had never spontaneously generated those expressions in the first place.
To a certain extent, it seems that the way we display our emotions really might come to us naturally.
Hackers Find Exploit and Reactivate LizardSquad’s Twitter Account
On September 2, hackers calling themselves “Spain Squad” used an exploit to take control of several previously suspended Twitter accounts. Among these accounts were usernames like @Hitler, @botnet, @LizardSquad and @1337. Twitter re-suspended all of the breached accounts shortly after the hack, but it is unclear whether or not they are still vulnerable to this exploit.
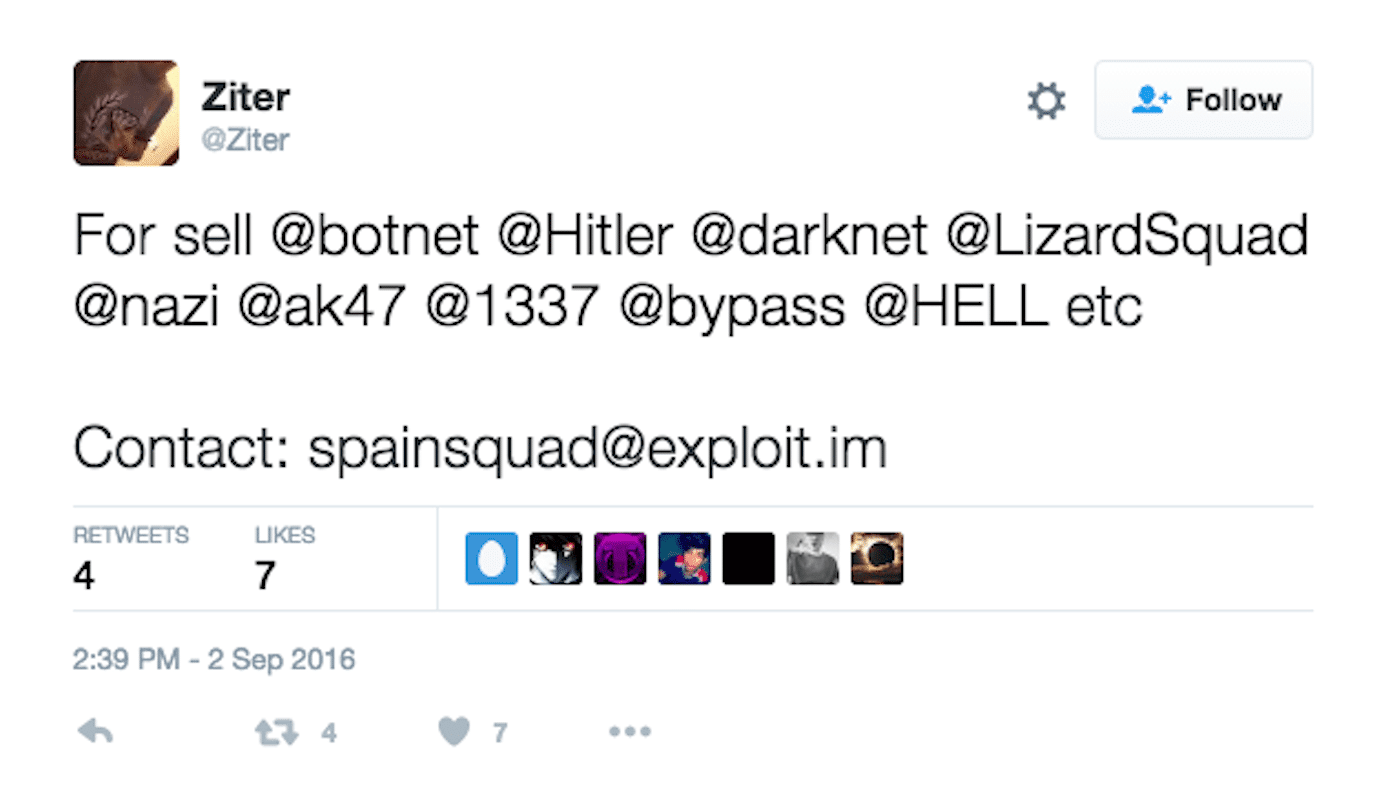
One of the hackers aligned with Spain Squad tweets about reactivated accounts.
“It could be a vulnerability in Twitter’s software, a compromised staff account, or some other explanation. It’s also unclear whether the exploit is still active, or was patched concurrently with the banning of the hijacked accounts.” (Business Insider)
A spokesperson for the hacking group has stated they can do even more than recover old accounts with the exploit they found:
“The new exploit allows Spain Squad to change to suspend active accounts, change a user’s Twitter handle and even take control of active accounts. So far, the group has only demonstrated the ability to recover officially suspended accounts — though all of those have already been re-suspended by the social media company.” (Engadget)
Twitter actively suspends accounts that violate their Terms of Service (TOS). Sometimes these suspensions can be temporary and the user is able to restore their account after acknowledging broken rules and promising not to violate TOS again. Often, the user must delete offending tweets before the account will be restored. Alternatively, a Twitter account can become permanently suspended, which means the account is never to be restored under any circumstances. Restoring access to accounts that were thought to be never again accessible could prove to be profitable for hackers selling screen names that may be valuable. However Spain Squad claims to be non-malicious. Whatever their intent, they were definitely doing some of it for the lulz when they took control of the LizardSquad account:
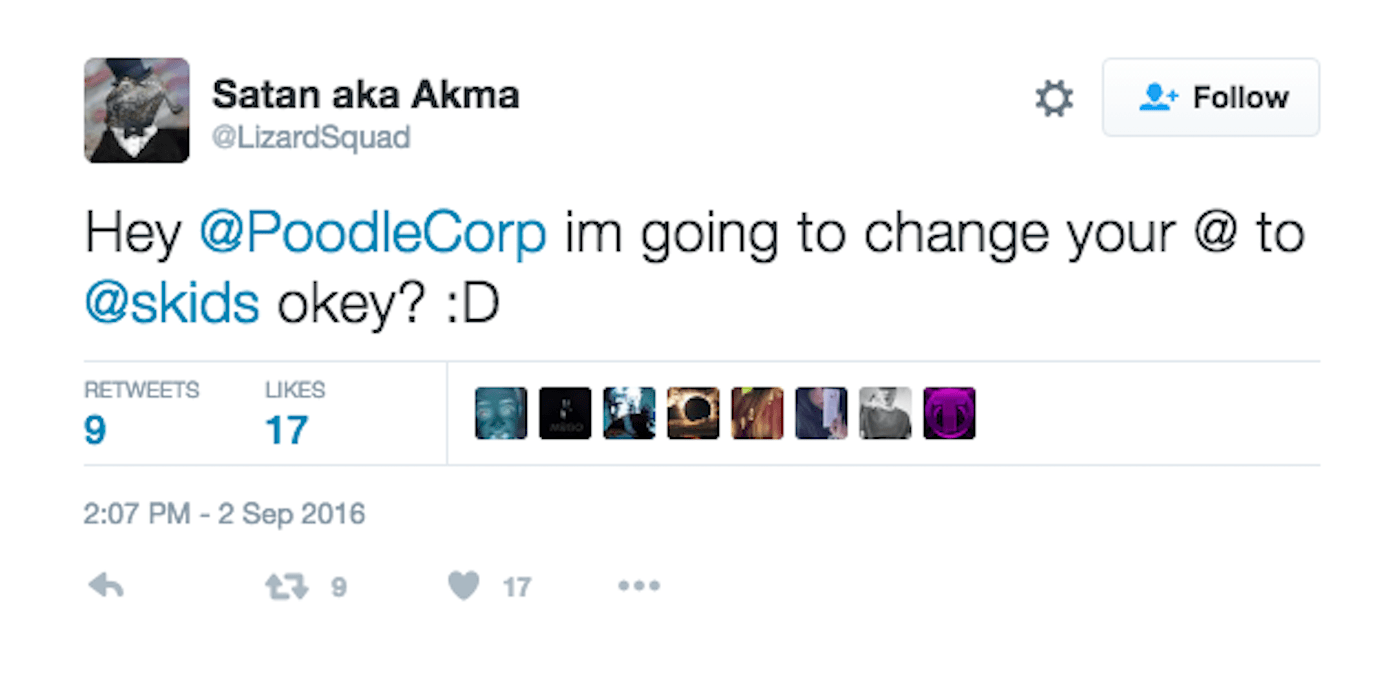
The post Hackers Find Exploit and Reactivate LizardSquad’s Twitter Account appeared first on Social Hax.
- « Previous Page
- 1
- …
- 124
- 125
- 126
- 127
- 128
- …
- 562
- Next Page »