Thought I would share some info on a text scam I got a few weeks ago. I setup a fake email account, got a burner number to make relevant calls and generated fake name, address, card number etc to see how these guys would respond.
Below is the original text message, I never win anything so imagine my amazement to win this Samsung promo 
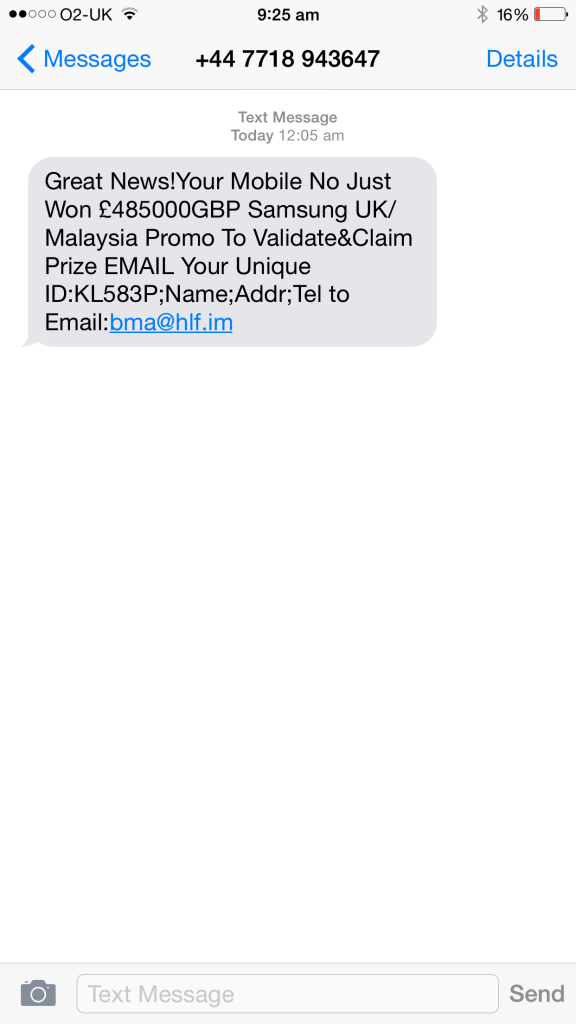
So with fake info created using various generators, and a new SIM card acquired I felt I must respond, I mean thats a nice win 
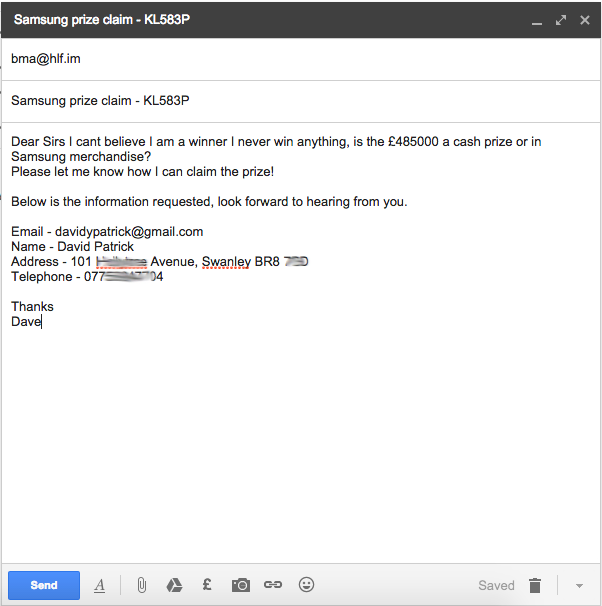
So I had provided them with all the info requested, so I just needed to wait for the cash to roll in. However surprisingly they asked for the same information again pretty much.
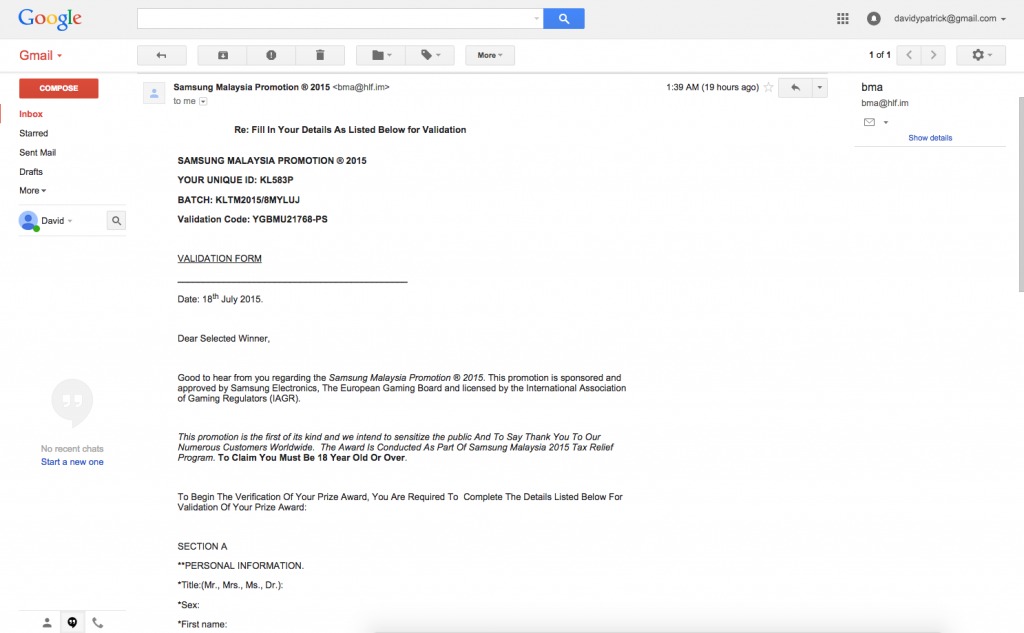
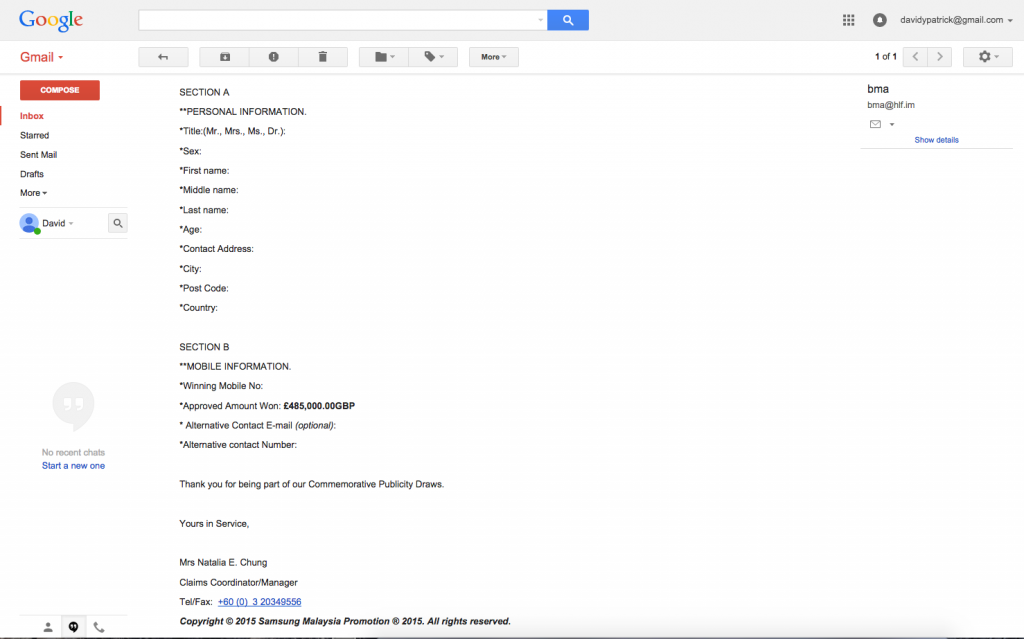
So … I provide all the needed info again and assume they will follow up asking for some form of payment, or credit card info to validate ID or something. But nothing  That was the end of it. So I can only assume they then look to utilise the data taken here for identity theft purposes. I have had other emails from the same number, so there isnt much intelligence going on in who they target, but if you get texts or emails similar to this, just delete them, share no info and respond to nothing.
That was the end of it. So I can only assume they then look to utilise the data taken here for identity theft purposes. I have had other emails from the same number, so there isnt much intelligence going on in who they target, but if you get texts or emails similar to this, just delete them, share no info and respond to nothing.
Today as I wrote this, I got another one on a different number, this time I have some money waiting for a recent accident claim I never had, just one magic click to cash in 
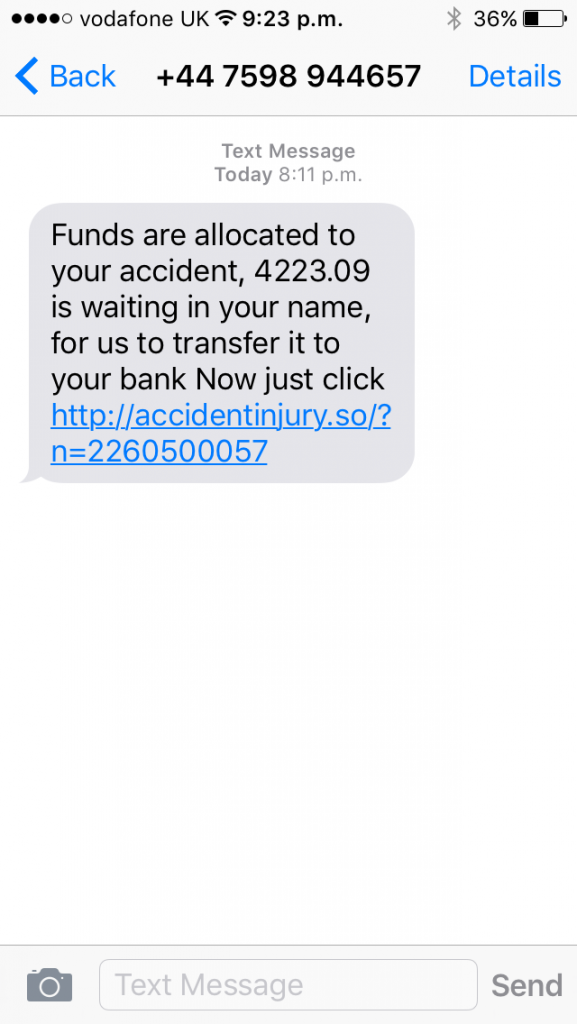
This isnt a particularly interesting post, more of a public service piece to share the numbers, email and site info so people get the scam results when searching, cheers for reading.
 There’s a Seinfeld episode in which Kramer orders some Cubans. Jerry thinks he’s ordering cigars but Kramer actually brought three Cuban men over so they could roll cigars for him. He didn’t get cigars because they were illegal.When America cut ties with Cuba after Fidel Castro took over, it became illegal to do business with Cuba. Whenever something is banned or difficult to get all of a sudden people want the banned or difficult to get things even more. That’s the principle of scarcity at work on the human psyche. Here are just a few examples.There was a point in time when you could only get Coors beer west of the Rockies. As a kid I remember my dad and his brothers talking about how good Coors was when they could get it. None of them drinks Coors now.Yuengling is another example of a beer that was hard to come by, at least in Ohio, until recent years. I recall traveling with a friend who made it a point to stop at a conveience store in West Virginia just to buy a case of Yuengling. Twinkies started flying off the shelf when it was announced Hostess was discontinuing the cake-filled treat.Back in 2001, Oldsmobile exceeded it sales goal by a higher percentage than better-known brands such as BMW, Kia, Porsche and many others, when it was announced the car line was being discontinued.I’m a Scotch lover and asked an expert at a tasting event his thoughts on aged Scotch (25 years and older). He said he tries a glass but doesn’t buy a bottle because age doesn’t necessarily mean better taste. He said the reason the price is so much higher for aged Scotch is just because there’s less of it. Why do we naturally feel compelled to take advantage of scarce resources or opportunities? From Influence Science and Practice:“One prominent theory accounts for the primacy of loss over gain in evolutionary terms. If one has enough to survive, an increase in resources will be helpful but a decrease in those same resources could be fatal. Consequently, it would be adaptive to be especially sensitive to the possibility of loss.” (Haselton & Nettle, 2006) Now here’s the interesting thing – once something is no longer scarce we don’t want it as much. There’s a good chance we’ll see this play out with Cuban cigars. Now that relations between the U.S. and Cuba have been normalized it’s a sure bet Cuban cigars will be easier to get. In all likelihood there will be a rush to get them when they initially hit the store shelves. However, as they become more commonplace it’s likely people won’t value them as much.Humans are not always predictable so there’s no guarantee I’m correct in my assessment of what will happen with Cuban cigar prices. Only time will tell. However, given how scarcity works on the human mind and surveying similar scenarios from the past, if I were a betting man I’d bet on a price fall shortly after Cubans – cigars that is – hit the U.S. market.
There’s a Seinfeld episode in which Kramer orders some Cubans. Jerry thinks he’s ordering cigars but Kramer actually brought three Cuban men over so they could roll cigars for him. He didn’t get cigars because they were illegal.When America cut ties with Cuba after Fidel Castro took over, it became illegal to do business with Cuba. Whenever something is banned or difficult to get all of a sudden people want the banned or difficult to get things even more. That’s the principle of scarcity at work on the human psyche. Here are just a few examples.There was a point in time when you could only get Coors beer west of the Rockies. As a kid I remember my dad and his brothers talking about how good Coors was when they could get it. None of them drinks Coors now.Yuengling is another example of a beer that was hard to come by, at least in Ohio, until recent years. I recall traveling with a friend who made it a point to stop at a conveience store in West Virginia just to buy a case of Yuengling. Twinkies started flying off the shelf when it was announced Hostess was discontinuing the cake-filled treat.Back in 2001, Oldsmobile exceeded it sales goal by a higher percentage than better-known brands such as BMW, Kia, Porsche and many others, when it was announced the car line was being discontinued.I’m a Scotch lover and asked an expert at a tasting event his thoughts on aged Scotch (25 years and older). He said he tries a glass but doesn’t buy a bottle because age doesn’t necessarily mean better taste. He said the reason the price is so much higher for aged Scotch is just because there’s less of it. Why do we naturally feel compelled to take advantage of scarce resources or opportunities? From Influence Science and Practice:“One prominent theory accounts for the primacy of loss over gain in evolutionary terms. If one has enough to survive, an increase in resources will be helpful but a decrease in those same resources could be fatal. Consequently, it would be adaptive to be especially sensitive to the possibility of loss.” (Haselton & Nettle, 2006) Now here’s the interesting thing – once something is no longer scarce we don’t want it as much. There’s a good chance we’ll see this play out with Cuban cigars. Now that relations between the U.S. and Cuba have been normalized it’s a sure bet Cuban cigars will be easier to get. In all likelihood there will be a rush to get them when they initially hit the store shelves. However, as they become more commonplace it’s likely people won’t value them as much.Humans are not always predictable so there’s no guarantee I’m correct in my assessment of what will happen with Cuban cigar prices. Only time will tell. However, given how scarcity works on the human mind and surveying similar scenarios from the past, if I were a betting man I’d bet on a price fall shortly after Cubans – cigars that is – hit the U.S. market. Brian Ahearn, CMCT® Chief Influence Officer influencePEOPLE Helping You Learn to Hear “Yes”.
Brian Ahearn, CMCT® Chief Influence Officer influencePEOPLE Helping You Learn to Hear “Yes”.