//
Click here to view the embedded video.
Humintell Director Dr. Matsumoto sat down with photographer Kris Davidson for an interview at the Academy of Art University in San Francisco California. Produced for an MFA level documentary photography course, Dr. Matsumoto shares valuable insights on the potential of a photograph to serve as a reliable document of truth.
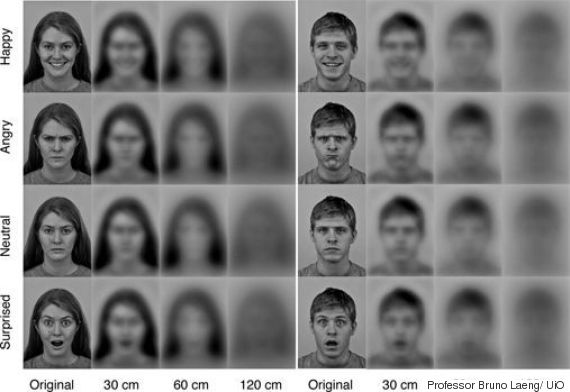 For the first time ever, scientists in Sweden and Norway have simulated how our emotional expressions appear to the dewy eyes of a newborn — and their finding may lay to rest a longstanding debate.
For the first time ever, scientists in Sweden and Norway have simulated how our emotional expressions appear to the dewy eyes of a newborn — and their finding may lay to rest a longstanding debate.