“You can fool some of the people all of the time, and all of the people some of the time, but you cannot fool all of the people all of the time.” –Abraham Lincoln  By: David EllisAre you sure that email from UPS is actually from UPS? (Or Costco, BestBuy, or the myriad of unsolicited emails you receive every day?) Companies and individuals are often targeted by cybercriminals via emails designed to look like they came from a legitimate bank, government agency, or organization. In these emails, the sender asks recipients to click on a link that takes them to a page where they will confirm personal data, account information, etc.
By: David EllisAre you sure that email from UPS is actually from UPS? (Or Costco, BestBuy, or the myriad of unsolicited emails you receive every day?) Companies and individuals are often targeted by cybercriminals via emails designed to look like they came from a legitimate bank, government agency, or organization. In these emails, the sender asks recipients to click on a link that takes them to a page where they will confirm personal data, account information, etc.
© SecurityMetrics | www.securitymetrics.com/pci | 801.705.5665 |
Hey guys, and welcome back to the SecurityQ, your source for business data security. Today on the SecurityQ, I want to cover one question. Are your employees properly trained to protect your business against phishing attacks? Not that type of fishing! Phishing is another tool used by hackers to gain access to your personal data. Phishing relies on your employees willingness to provide sensitive information like passwords, bank, and tax information. Here’s how it works. Companies are targeted via an email that is designed to look like it comes from a legitimate bank, organization our government agency. Then the sender asks to confirm personal information, in essence, phishing for data. For example. Let’s say your business does e-commerce through Pay Pal. Hackers posing as PayPal will contact you via email asking you to confirm sensitive information pertaining to your account. Once information is obtained, hackers use the credentials gained to steal your sensitive data mostly through attacks like malware and back doors to your network. That’s hook, line, and sinker. The scary thing is, you may have the best technology in the world but if your employees aren’t properly trained, that technology is a complete and utter waste. Currently twenty percent of all breaches now involve phishing. Everyone in every industry and every company is ultimately a target. Keep in mind, it takes only one untrained employees to give away all the data you worked so hard to protect. As a business owner, how can you detect phishing attacks and properly train employees? First the message or email you’re receiving may appear entirely convincing. You should keep a lookout for three things. Layout issues, spelling , and grammatical issues, go hand in hand with phishing attacks. Second don’t just check the name of the person sending email. You need to check the email address and ensure that there are no alterations made to it. For example, additional letters for numbers added to the email address. Last, most companies will never ask for your personal information through email. If there’s any doubt, contact the sender. Remember, even savvy technology users can find themselves fooled by messages that appear authentic so be cautious, Our advice? Educate your employees about phishing attacks. When it comes to staying safe online, it never hurts have a little bit a cynicism. Well guys, that’s all the time we have for today on the SecurityQ, but as always we want to hear from you. So post your questions in the comments below, and don’t forget to subscribe. See ya next time on the SecurityQ.wistiaEmbed = Wistia.embed(“exi3oxmnof”); This technique is called phishing, and it’s a way hackers con you into providing your personal information or account data. Once your info is obtained, hackers create new user credentials or install malware (such as backdoors) into your system to steal sensitive data. SEE ALSO: Examples of common phishing attempts.It’s often difficult to distinguish a fake email from a verified one, however most have subtle hints of their scammy nature. Here are seven ways to help you recognize a phishing email and maintain email security.1. Legit companies don’t request your sensitive information via emailChances are if you receive an unsolicited email from an institution that provides a link or attachment and asks you to provide sensitive information, it’s a scam. Most companies will not send you an email asking for passwords, credit card information, credit scores, or tax numbers, nor will they send you a link from which you need to login. 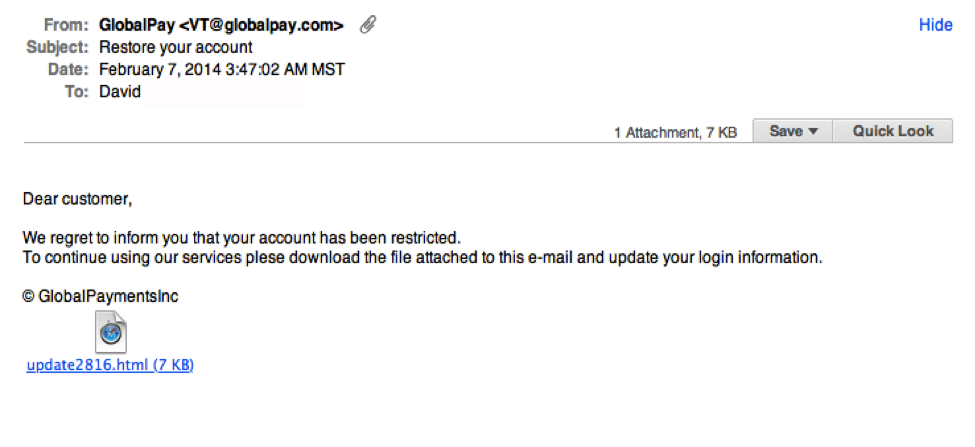 Notice the generic salutation at the beginning, and the unsolicited web link attachment?2. Legit companies call you by your namePhishing emails typically use generic salutations such as “Dear valued member,” “Dear account holder,” or “Dear customer.” If a company you deal with required information about your account, the email would call you by name and probably direct you to contact them via phone.
Notice the generic salutation at the beginning, and the unsolicited web link attachment?2. Legit companies call you by your namePhishing emails typically use generic salutations such as “Dear valued member,” “Dear account holder,” or “Dear customer.” If a company you deal with required information about your account, the email would call you by name and probably direct you to contact them via phone. Sir/Madam? Also, what’s up with the 17 in the middle of the sentence?3. Legit companies have domain emailsDon’t just check the name of the person sending you the email. Check their email address by hovering your mouse over the ‘from’ address. Make sure no alterations (like additional numbers or letters) have been made. Check out the difference between these two email addresses as an example of altered emails: [email protected] [email protected] Just remember, this isn’t a foolproof method. Sometimes companies make use of unique or varied domains to send emails, and some smaller companies use third party email providers.
Sir/Madam? Also, what’s up with the 17 in the middle of the sentence?3. Legit companies have domain emailsDon’t just check the name of the person sending you the email. Check their email address by hovering your mouse over the ‘from’ address. Make sure no alterations (like additional numbers or letters) have been made. Check out the difference between these two email addresses as an example of altered emails: [email protected] [email protected] Just remember, this isn’t a foolproof method. Sometimes companies make use of unique or varied domains to send emails, and some smaller companies use third party email providers.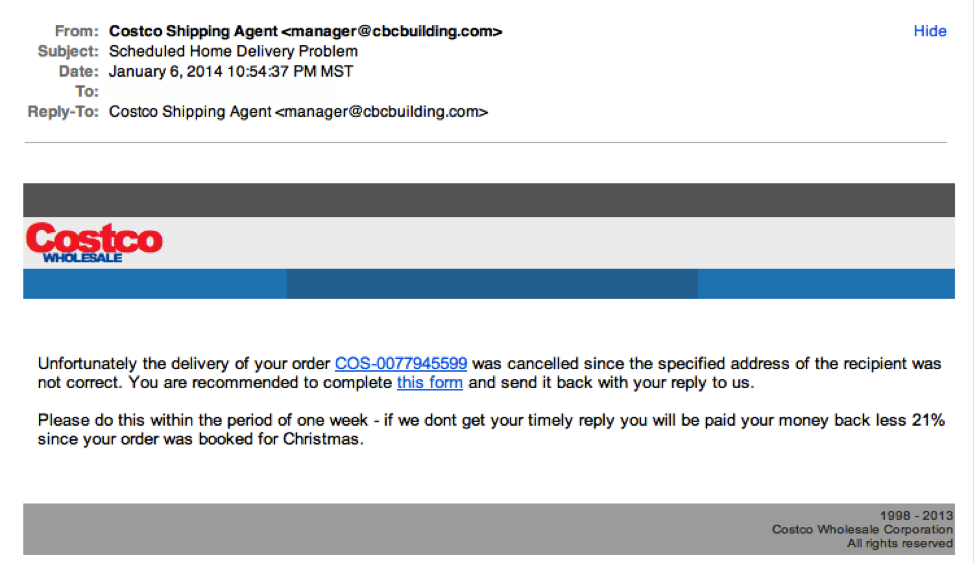 “Costco’s” logo is just a bit off. This is what the Costco logo is supposed to look like.
“Costco’s” logo is just a bit off. This is what the Costco logo is supposed to look like. See the difference? Subtle, no? 4. Legit companies know how to spellPossibly the easiest way to recognize a scammy email is bad grammar. An email from a legitimate organization should be well written. Little known fact – there’s actually a purpose behind bad syntax. Hackers generally aren’t stupid. They prey on the uneducated because they are easier targets.
See the difference? Subtle, no? 4. Legit companies know how to spellPossibly the easiest way to recognize a scammy email is bad grammar. An email from a legitimate organization should be well written. Little known fact – there’s actually a purpose behind bad syntax. Hackers generally aren’t stupid. They prey on the uneducated because they are easier targets.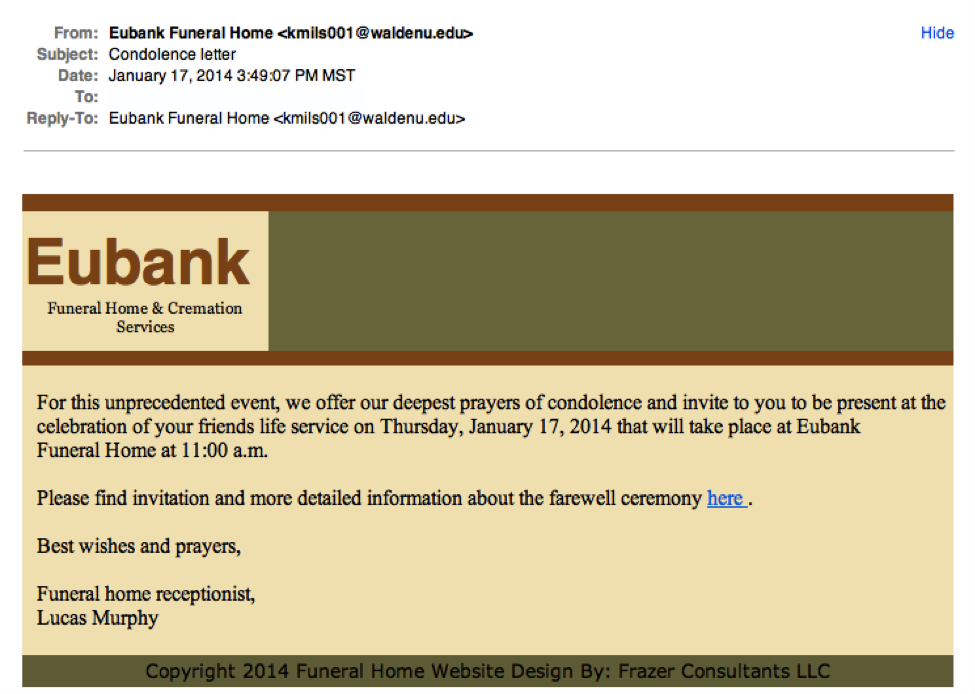 Notice the apostrophe in the word ‘friends’? Me neither. Other than that tiny grammar mistake, this is a very convincing email. 5. Legit companies don’t force you to their websiteSometimes phishing emails are coded entirely as a hyperlink. Therefore, clicking accidentally or deliberately anywhere in the email will open a fake web page, or download spam onto your computer.
Notice the apostrophe in the word ‘friends’? Me neither. Other than that tiny grammar mistake, this is a very convincing email. 5. Legit companies don’t force you to their websiteSometimes phishing emails are coded entirely as a hyperlink. Therefore, clicking accidentally or deliberately anywhere in the email will open a fake web page, or download spam onto your computer.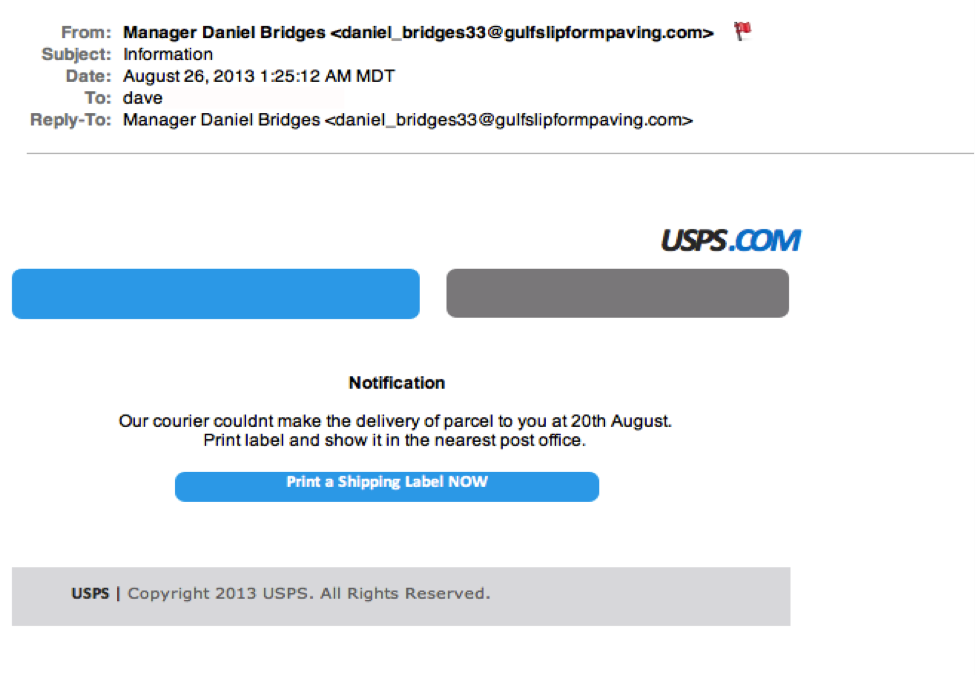 This whole email is likely a gigantic hyperlink. 6. Legit companies don’t send unsolicited attachmentsUnsolicited emails that contain attachments reek of hackers. Typically, authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website.
This whole email is likely a gigantic hyperlink. 6. Legit companies don’t send unsolicited attachmentsUnsolicited emails that contain attachments reek of hackers. Typically, authentic institutions don’t randomly send you emails with attachments, but instead direct you to download documents or files on their own website. ![]() Like the tips above, this method isn’t foolproof. Sometimes companies that already have your email will send you information, such as a white paper, that may require a download. In that case, be on the lookout for high-risk attachment file types include .exe, .scr, and .zip. (When in doubt, contact the company directly using contact information obtained from their actual website.)
Like the tips above, this method isn’t foolproof. Sometimes companies that already have your email will send you information, such as a white paper, that may require a download. In that case, be on the lookout for high-risk attachment file types include .exe, .scr, and .zip. (When in doubt, contact the company directly using contact information obtained from their actual website.)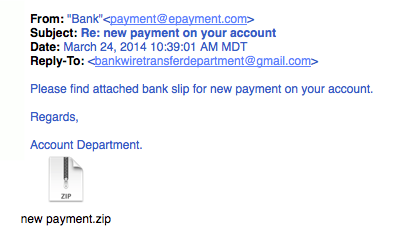 Just remember, curiosity killed the cat.7. Legit company links match legitimate URLsJust because a link says it’s going to send you to one place, doesn’t mean it’s going to. Double check URLs. If the link in the text isn’t identical to the URL displayed as the cursor hovers over the link, that’s a sure sign you will be taken to a site you don’t want to visit. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it. Ensure additional security by hovering your mouse over embedded links (without clicking!) and ensure the link begins with https://.
Just remember, curiosity killed the cat.7. Legit company links match legitimate URLsJust because a link says it’s going to send you to one place, doesn’t mean it’s going to. Double check URLs. If the link in the text isn’t identical to the URL displayed as the cursor hovers over the link, that’s a sure sign you will be taken to a site you don’t want to visit. If a hyperlink’s URL doesn’t seem correct, or doesn’t match the context of the email, don’t trust it. Ensure additional security by hovering your mouse over embedded links (without clicking!) and ensure the link begins with https://.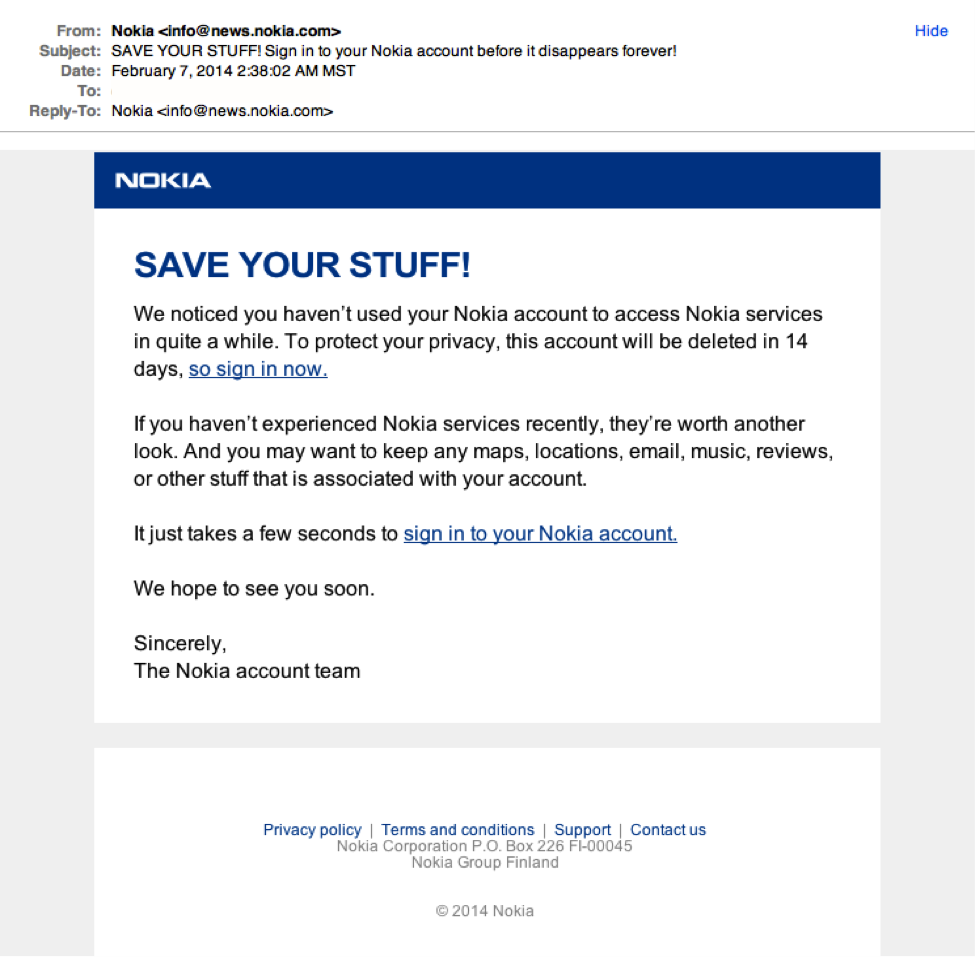 Although very convincing, the real Nokia wouldn’t be sending you a “Save your stuff” email from [email protected] doesn’t matter if you have the most secure security system in the world. It takes only one untrained employee to be fooled by a phishing attack and give away the data you’ve worked so hard to protect. Make sure both you and your employees understand the telltale signs of a phishing attempt.Was this post helpful? If so, please share!wistiaEmbed = Wistia.embed(“exi3oxmnof”); David Ellis (GCIH, QSA, PFI, CISSP) is Director of Forensic Investigations at SecurityMetrics with over 25 years of law enforcement and investigative experience. Check out his other blog posts.
Although very convincing, the real Nokia wouldn’t be sending you a “Save your stuff” email from [email protected] doesn’t matter if you have the most secure security system in the world. It takes only one untrained employee to be fooled by a phishing attack and give away the data you’ve worked so hard to protect. Make sure both you and your employees understand the telltale signs of a phishing attempt.Was this post helpful? If so, please share!wistiaEmbed = Wistia.embed(“exi3oxmnof”); David Ellis (GCIH, QSA, PFI, CISSP) is Director of Forensic Investigations at SecurityMetrics with over 25 years of law enforcement and investigative experience. Check out his other blog posts.
 Day after day, on social media and elsewhere on the Internet, there are lots of folks who are seemingly shocked every time a bad guy shows up and acts like a bad guy. Seriously, how many times have you read or seen “I can’t believe Suspect A was able to murder all of those people” or “If only they (security) did XYZ like I thought of during a conversation with my veterinarian who may have been in the military, that bad thing wouldn’t have happened”? I see it quite a bit and frankly, I’ve decided it may be time to finally add my .02 about it.Those of us in security who have spent some time studying “the threat” (insert whatever scary bad guy you’re dealing with) understand what few who haven’t studied it don’t. No matter how awesome your protective measures are, they do little to mitigate (and certainly not “prevent”) the attacker unless you start thinking a bit like they do. Herein lies the fatal flaw of most “white hats” and even some “grey hats”.You think of attacks in ways that you would conduct them. No offense but if you’re protecting yourself against robbers but know relatively little of them, you may be looking to deploy solutions which don’t work against that threat. One of the most painful things any security professional can hear when doing a site survey with a client from the client is “If I were the bad guy, this is how I would do it.” More often than not, it is not how the bad guys would attack. Think security cameras in homes. Most people will deploy a camera at home with the thought the camera provides an extra layer of protection when in fact it doesn’t. I have known several victims of home invasions who either had cameras installed or had an alarm sign out front. These are two commonly deployed deterrence tools that we know don’t work. Instead, focus on the problem as if the bad guy would ignore the deterrence measures (because he will because we have little proof he won’t) and proceed with the attack and use things like cameras as after-incident mitigation tools to catch the perpetrator later.You think of your threat as one-dimensional. Most good guys see their threat based on commonly accepted precepts of what the threat is and how he has attacked in the past. Just because the bad guy only hit you or the other guy using one vector doesn’t mean he won’t try something different later. A great example of this is 9/11. Prior to the second World Trade Center attack, there were common beliefs that terrorists were only capable of performing certain kinds of attacks. What no factored in was changing realistic threat capabilities. In other words, we assumed the threat wasn’t evolutionary in his tactics. Seriously, who could’ve imagine having to protect a building against two near-simultaneous aircraft crashes? Perhaps we could have had we accepted the idea that as we change so does the threat.You think the threat is omnipotent and omnipresent. It’s easy to get caught up in the hype of a threat. I do it sometimes. This is a natural defense mechanism after an attack has occurred. Why? No one likes to have their vulnerabilities exposed. After every mass shooting or act of violence that makes the news, we assume every venue that is like the one that was attacked is also vulnerable and being selected as the “next” target for another perpetrator.I remember fondly working on 9/11 on a small Air Force base on a perimeter patrol. What I recall the most are the initial attitudes people had of al Qaeda. We believed this one attack displayed a level of sophistication unseen by them before on US soil could be replicated on a massive scale. Every Muslim, ignorantly, was assumed to be a sleeper agent waiting for cues from “Muslim HQ” to attack us wherever and however they chose. The months and years ahead showed how far from the truth that was. Imagine how many countless resources were expended before we realized the fallacy behind this assumption.You think your attacker “chose” you for a variety of reasons he didn’t. People almost always assume an attacker chose to attack them or others for reasons they didn’t. Rape is commonly thought to be a crime of lust because good people believe sex is the only reason you rape because it’s the end-result. However, most criminologists and psychologists would agree rape is a crime of power. I would argue the majority of crime takes place for this very reason. Terrorism occurs because of this as does murder (what’s more powerful than ridding yourself of someone permanently), drug dealing, fraud, and a host of other crimes. You’re either fighting to obtain it (i.e. steal it from someone else) or committing crime to become more powerful. This confusion could possibly explain why most crime “prevention” measures based on policy fail at alarming rates – we’re clueless on what truly motivates people to attack us.You assume because you haven’t seen the threat, he must not exist. Whether we see the threat or not, we should never assume he does not exist. While the threat can’t be everywhere every time, the threat can still be very much. Never assume the absence of threat means he or she isn’t going to show. You still need to adequately protect your assets as if today is the day you’re going to be attacked. Remember, the attacker chooses the time of attack. You choose how well-prepared you’ll be when it happens.I’m not proposing anyone go out and hire a red team. I firmly believe one of the reasons we, often, fail so miserably at security sometimes is due to our natural inclination to think the bad guy thinks like we do when they don’t. So how can we fix this?Study your adversary. Seriously, pour over any open source intelligence you can on your threat. Read the paper and look for crime stories. Pick up a police report or two on similar venues like yours. I’ll leave how you conduct your research to you. Just do it. Stop assuming blindly how the attack will go down or even who your adversary is.Consider hiring folks who can think like attackers. I’m not saying you hire criminals but red teams hire specialists who can mimic attackers. Choose folks from a variety of backgrounds to round out your security team. By the way, by “background”, I’m not talking education. I mean pick a team with a variety of specialists.Test your systems with exercises. The only way you’re going to learn is by testing how well your security program holds up against an actual attack. Consider doing this with little to no notice and have an after-action or “hot-wash” debriefing with your red team and affected staff right away. Finally, fix the vulnerabilities as soon as possible.Reward outside the box thinking. When I was a young boy, I recall my fondest memories were playing games like “hide-and-go-seek” with my friends. The guys who were the most creative were the best at this game. Why? Because they were unpredictable. I’ll leave how you choose to reward these folks on your own. Just do it.
Day after day, on social media and elsewhere on the Internet, there are lots of folks who are seemingly shocked every time a bad guy shows up and acts like a bad guy. Seriously, how many times have you read or seen “I can’t believe Suspect A was able to murder all of those people” or “If only they (security) did XYZ like I thought of during a conversation with my veterinarian who may have been in the military, that bad thing wouldn’t have happened”? I see it quite a bit and frankly, I’ve decided it may be time to finally add my .02 about it.Those of us in security who have spent some time studying “the threat” (insert whatever scary bad guy you’re dealing with) understand what few who haven’t studied it don’t. No matter how awesome your protective measures are, they do little to mitigate (and certainly not “prevent”) the attacker unless you start thinking a bit like they do. Herein lies the fatal flaw of most “white hats” and even some “grey hats”.You think of attacks in ways that you would conduct them. No offense but if you’re protecting yourself against robbers but know relatively little of them, you may be looking to deploy solutions which don’t work against that threat. One of the most painful things any security professional can hear when doing a site survey with a client from the client is “If I were the bad guy, this is how I would do it.” More often than not, it is not how the bad guys would attack. Think security cameras in homes. Most people will deploy a camera at home with the thought the camera provides an extra layer of protection when in fact it doesn’t. I have known several victims of home invasions who either had cameras installed or had an alarm sign out front. These are two commonly deployed deterrence tools that we know don’t work. Instead, focus on the problem as if the bad guy would ignore the deterrence measures (because he will because we have little proof he won’t) and proceed with the attack and use things like cameras as after-incident mitigation tools to catch the perpetrator later.You think of your threat as one-dimensional. Most good guys see their threat based on commonly accepted precepts of what the threat is and how he has attacked in the past. Just because the bad guy only hit you or the other guy using one vector doesn’t mean he won’t try something different later. A great example of this is 9/11. Prior to the second World Trade Center attack, there were common beliefs that terrorists were only capable of performing certain kinds of attacks. What no factored in was changing realistic threat capabilities. In other words, we assumed the threat wasn’t evolutionary in his tactics. Seriously, who could’ve imagine having to protect a building against two near-simultaneous aircraft crashes? Perhaps we could have had we accepted the idea that as we change so does the threat.You think the threat is omnipotent and omnipresent. It’s easy to get caught up in the hype of a threat. I do it sometimes. This is a natural defense mechanism after an attack has occurred. Why? No one likes to have their vulnerabilities exposed. After every mass shooting or act of violence that makes the news, we assume every venue that is like the one that was attacked is also vulnerable and being selected as the “next” target for another perpetrator.I remember fondly working on 9/11 on a small Air Force base on a perimeter patrol. What I recall the most are the initial attitudes people had of al Qaeda. We believed this one attack displayed a level of sophistication unseen by them before on US soil could be replicated on a massive scale. Every Muslim, ignorantly, was assumed to be a sleeper agent waiting for cues from “Muslim HQ” to attack us wherever and however they chose. The months and years ahead showed how far from the truth that was. Imagine how many countless resources were expended before we realized the fallacy behind this assumption.You think your attacker “chose” you for a variety of reasons he didn’t. People almost always assume an attacker chose to attack them or others for reasons they didn’t. Rape is commonly thought to be a crime of lust because good people believe sex is the only reason you rape because it’s the end-result. However, most criminologists and psychologists would agree rape is a crime of power. I would argue the majority of crime takes place for this very reason. Terrorism occurs because of this as does murder (what’s more powerful than ridding yourself of someone permanently), drug dealing, fraud, and a host of other crimes. You’re either fighting to obtain it (i.e. steal it from someone else) or committing crime to become more powerful. This confusion could possibly explain why most crime “prevention” measures based on policy fail at alarming rates – we’re clueless on what truly motivates people to attack us.You assume because you haven’t seen the threat, he must not exist. Whether we see the threat or not, we should never assume he does not exist. While the threat can’t be everywhere every time, the threat can still be very much. Never assume the absence of threat means he or she isn’t going to show. You still need to adequately protect your assets as if today is the day you’re going to be attacked. Remember, the attacker chooses the time of attack. You choose how well-prepared you’ll be when it happens.I’m not proposing anyone go out and hire a red team. I firmly believe one of the reasons we, often, fail so miserably at security sometimes is due to our natural inclination to think the bad guy thinks like we do when they don’t. So how can we fix this?Study your adversary. Seriously, pour over any open source intelligence you can on your threat. Read the paper and look for crime stories. Pick up a police report or two on similar venues like yours. I’ll leave how you conduct your research to you. Just do it. Stop assuming blindly how the attack will go down or even who your adversary is.Consider hiring folks who can think like attackers. I’m not saying you hire criminals but red teams hire specialists who can mimic attackers. Choose folks from a variety of backgrounds to round out your security team. By the way, by “background”, I’m not talking education. I mean pick a team with a variety of specialists.Test your systems with exercises. The only way you’re going to learn is by testing how well your security program holds up against an actual attack. Consider doing this with little to no notice and have an after-action or “hot-wash” debriefing with your red team and affected staff right away. Finally, fix the vulnerabilities as soon as possible.Reward outside the box thinking. When I was a young boy, I recall my fondest memories were playing games like “hide-and-go-seek” with my friends. The guys who were the most creative were the best at this game. Why? Because they were unpredictable. I’ll leave how you choose to reward these folks on your own. Just do it. 